
Windows Password Recovery Lastic
Tip: Also you could try to use online password recovery service Password-Find

Tip: Also you could try to use online password recovery service Password-Find
Windows Password Recovery Lastic can instantly remove a user account password of any Windows OS installed on your computer (see System Requirements for more info).
On your screen you can see the partition of your disk. This indicates what operating system the program displays user account of. So if you have several Windows system installed on your computer you will be able to remove Windows passwords in any of them.
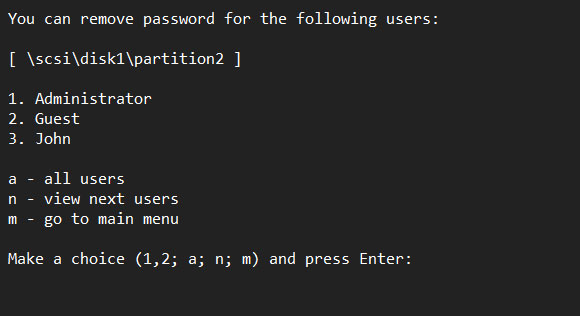
Type your choice (1,2,3 etc) to remove a password of a particular user – the name is displayed in the list – and press Enter. Or you can use the following shortcuts:
After you press Enter, Windows Password Recovery Lastic makes all necessary changes in the SAM files so the password or passwords of the selected user accounts will be removed. The process is instant. Additionally, the program creates a backup in the root directory of the disk where the corresponding OS is installed. This backup can be used to restore Windows password later.
Sometimes you may want to restore Windows password after it has been removed. Luckily, Windows Password Recovery Lastic creates a special backup.txt file in the root folder of the disk where the operating system is installed.
In order to restore the password, select the corresponding command in the main menu. The program displays the list of user accounts in all operating systems on all partitions it can find. Use numbers and shortcuts as described above to restore a password of a particular user only, or to restore all passwords at once.
In addition to removing Windows passwords, Windows Password Recovery Lastic allows you to save Windows password hashes (LM and NTLM). Hash is a numerical value constructed from the password string using certain mathematical functions. Windows doesn’t stores passwords directly, so you cannot just recover them. Instead, Windows stores hashes of passwords and use hashes to check if a correct password has been entered or not. Mathematically, hashes are not reversible, so it is impossible to find a password from its hash. Nevertheless, you can attempt to crack a password from saved hash files with the “brute-force” method using special tools like SAMInside or L0phtCrack.
The hashes are saved into the root folder of the USB flash drive, or to the root folder of the partition where Windows is installed if you boot from CD.
Password hashes are stored in the PWDump format:
[User]::[LM hash]:[NTLM hash]:::
Special cracking programs like SAMInside allow finding a password from PWDump hashes, but this operation is very time-consuming, so whenever you can – use Remove Windows password options instead – it is instant.
You can display restored Windows password hashes on your screen and write them down instead of saving them to a file.
Hashes are displayed in an easy-to-read format:
Administrator
aad3 b435 b514 04ee aad3 b435 b514 04ee
2d20 d252 a479 f485 cdf5 e171 d939 85bf ;
Guest
aad3 b435 b514 04ee aad3 b435 b514 04ee
3dbd e697 d716 90a7 6920 4beb 1228 3678 ;
But when you perform saving, hashes are written in the PWDump format:
[User]::[LM hash]:[NTLM hash]:::
Administrator::aad3b435b51404eeaad3b435b51404ee:2d20d252a479f485cdf5e171d93985bf:::
Guest::aad3b435b51404eeaad3b435b51404ee:3dbde697d71690a769204beb12283678:::
Using special programs like SAMInside or L0phtCrack you can attempt to crack those hashes and discover the password.